Contents
Duo supports multiple solutions for adding two-factor authentication to Microsoft's online services like Microsoft 365, Office 365, and Entra ID. Learn more about these configurations and choose the best option for your organization.
Duo External Authentication Method for Entra ID External Authentication Methods (EAM)
Microsoft customers with subscription plans that include Entra ID Premium P1 or P2 can secure Microsoft 365 and Entra ID logons with Duo as an external multifactor authentication method. Apply conditional access policies which require MFA to Entra ID users, groups, applications, login contexts, and many other categories. Microsoft MFA policies will offer Duo as an option for identity verification.
This solution does not require any Duo software deployed on-premises. After your end users complete primary Entra ID authentication they will be redirected to Duo's cloud service to complete two-factor authentication, and subsequently redirected back to Microsoft's service.
Read the deployment instructions for Duo as an Entra ID External Authentication Method.
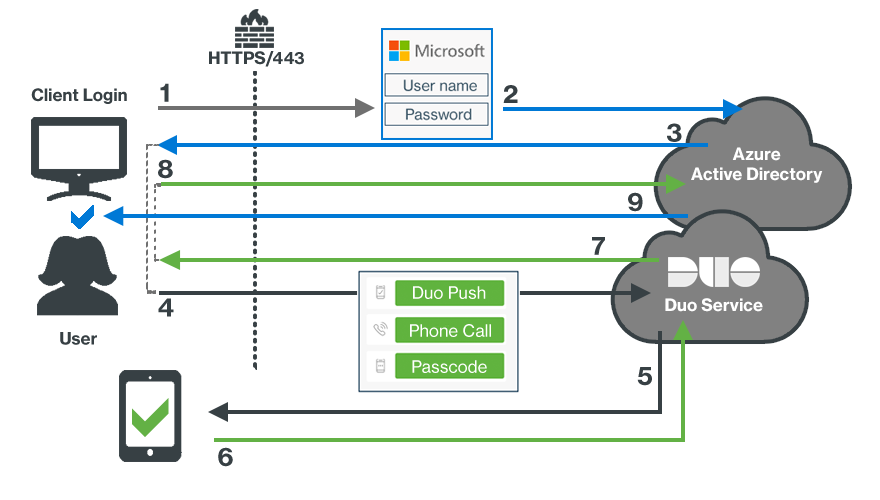
- User accesses Microsoft Online or other services using Entra ID authentication.
- User submits primary Entra ID credentials.
- User selects the Duo EAM method, which redirects the client browser to Duo.
- User receives the Duo Prompt and submits factor selection.
- User receives Duo Push authentication request on device.
- Authentication approval returned to Duo service.
- Secondary authentication approval returned to client.
- Client sends Duo approval back to Entra ID.
- Entra ID grants application or service access once the MFA requirement and all other aspects of the user's effective conditional access policy is satisfied.
Single Sign-On with Duo Single Sign-On
Duo Single Sign-on is a cloud-hosted Security Assertion Markup Language (SAML) 2.0 SSO solution that adds two-factor authentication to Microsoft 365 and Azure logins. Duo Single Sign-On acts as an identity provider (IdP), authenticating your users using existing on-premises Active Directory (AD) credentials and prompting for two-factor authentication before permitting access to Microsoft 365.
This solution requires deployment of the Duo Authentication Proxy on your internal network to verify primary logon credentials against Active Directory. Your end users will sign in and perform two-factor authentication at Duo's cloud-hosted SSO service, and do not contact the on-premises Authentication Proxy servers directly.
Read the deployment instructions for Duo Single Sign-On for Microsoft 365
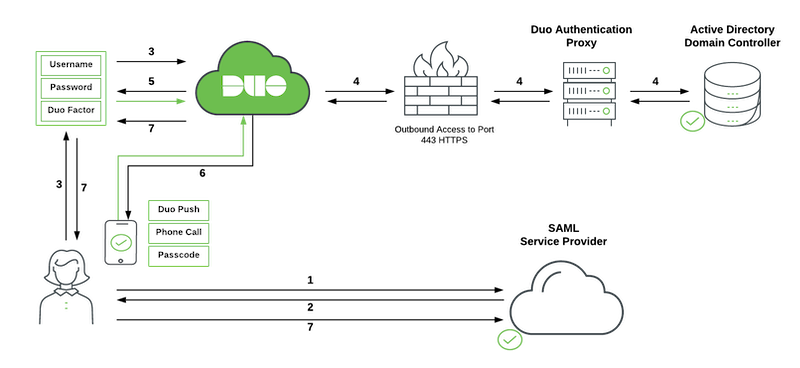
- User accesses Microsoft Online or other services using Azure authentication and submits a username to Azure from a domain federated with Duo SSO.
- Azure redirects the user's browser to Duo Single Sign-On with a SAML request message.
- User logs in with primary credentials.
- Duo Single Sign-On sends the credentials to the Duo Authentication Proxy deployed on-premises. The Authentication Proxy verifies the user's credentials against Active Directory and sends the response back to Duo Single Sign-On.
- Duo Single Sign-On requires the user to complete two-factor authentication.
- User completes Duo two-factor authentication.
- Duo Single Sign-On redirects the user's browser back to the SAML Service Provider (Azure) with response message.
Single Sign-On with Duo Access Gateway
Duo Access Gateway (DAG), our on-premises SSO product, layers Duo's strong authentication and flexible policy engine on top of Microsoft 365 logins using the Security Assertion Markup Language (SAML) 2.0 authentication standard. Duo Access Gateway acts as an identity provider (IdP), authenticating your users using existing on-premises Active Directory (AD) credentials and prompting for two-factor authentication before permitting access to Microsoft 365.
This solution requires deployment of a web server with Duo Access Gateway in your DMZ. Your end users will sign in and perform two-factor authentication at the Duo Access Gateway server when signing in to Microsoft online services and applications.
Read the deployment instructions for Microsoft 365 SSO with Duo Access Gateway
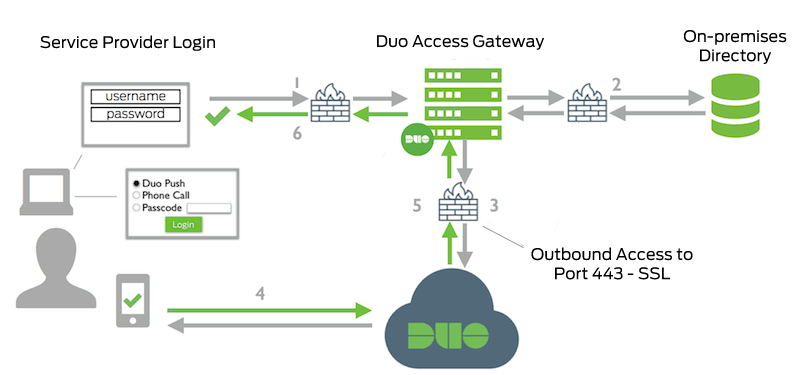
- User accesses Microsoft Online or other services using Azure authentication and submits a username to Azure from a federated domain. Azure redirects the user to Duo Access Gateway.
- Primary authentication to on-premises Active Directory.
- Duo Access Gateway connection established to Duo Security over TCP port 443.
- Secondary authentication via Duo Security’s service.
- Duo Access Gateway receives authentication response.
- Duo Access Gateway redirects the user's browser back to the SAML Service Provider (Azure) with response message.
Duo Multifactor for Microsoft Active Directory Federation Services
Customers who have already federated Entra ID with on on-premises Microsoft Active Directory Federation Services (AD FS) deployment for SSO can install Duo's multifactor authentication (MFA) adapter for AD FS. This lets you add Duo as a required MFA method for users signing in to AD FS, where they will complete Duo two-factor authentication after primary username and password verification at AD FS.
This solution requires installation of the Duo MFA adapter on each AD FS server, whether they are standalone or in a farm deployment.
Read the deployment instructions for Duo Authentication for Microsoft AD FS
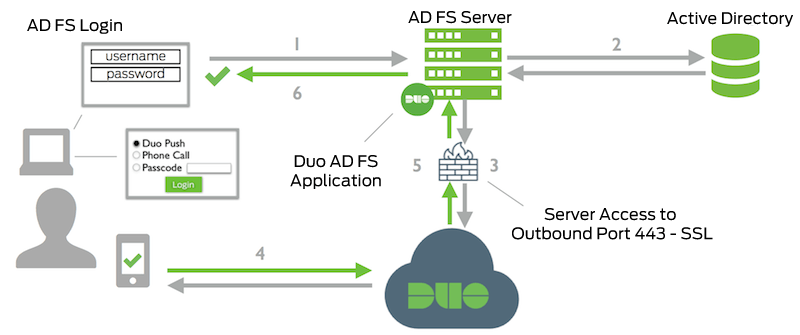
- User accesses Microsoft Online or other services using Azure authentication and submits a username to Azure from a federated domain. Azure redirects the user to AD FS.
- Primary authentication to Active Directory
- Duo AD FS adapter connection established to Duo Security over TCP port 443
- Secondary authentication via Duo Security’s service
- AD FS MFA claim featuring the Duo adapter satisfied.
- AD FS session logged in and Azure access granted.
Single Sign-On with Third-Party Identity Providers
Duo has partnered with leading identity providers to offer two-factor authentication in those services. Learn more about using Duo with these third-party IdPs:
Guidance for Federal and Government Customers
Microsoft’s Government Cloud does not support custom controls for conditional access in Azure Government’s Active Directory service. In addition, Duo Federal plans do not yet include Duo Single Sign-On. Federal customers should consider deploying Duo Access Gateway, Microsoft AD FS, or another on-premises SSO solution to protect Azure Government/GCC tenants with Duo two-factor authentication.
