Zero Trust Application Access: Protecting Against Compromised Endpoints
In today's interconnected world, ensuring robust security measures is crucial. One of the key aspects of application security is endpoint security, which focuses on protecting the devices that access these applications. This blog explores why endpoint security is of utmost importance when accessing applications and highlights the potential risks associated with compromised endpoints.
Before we dive into the threats caused by compromised endpoints, let’s quickly take a look at the recipe for a successful protection strategy:
Access devices that have an installed Cisco Secure Endpoint Connector
Any paid edition of Duo (Essentials, Advantage or Premier) using Trusted Endpoints
A Duo Care team that’s got your back by providing security policy planning, solution architecture consulting, best practices guidelines and much more

The growing threat landscape
The digital landscape is teeming with threats, ranging from malware and ransomware to phishing attacks. Compromised endpoints act as an entry point for these malicious actors, enabling them to infiltrate the entire application ecosystem. By implementing advanced endpoint security measures, such as the Cisco Secure Endpoint integration with Duo Trusted Endpoints, organizations can significantly reduce the risk of such breaches.
Protecting sensitive data
Applications often contain highly sensitive information, including financial data, customer details, and intellectual property. When endpoints lack adequate security measures, unauthorized individuals can gain access to this valuable data, resulting in severe consequences such as financial loss, reputational damage, and compliance violations. Endpoint security ensures that only authorized users with secure devices can access critical applications, reducing the risk of data compromise. If an access device is marked as compromised within the Cisco Secure Endpoint Dashboard, Duo can outright block the application access attempt. Check out the Cisco article Configure Duo and Secure Endpoint to Respond to Threats.
Enforcing a zero trust model
A Zero Trust Architecture model advocates for a "never trust, always verify" approach to security. It assumes that every user and device is potentially compromised and requires continuous authentication and authorization. Endpoint security plays a pivotal role in enforcing the Zero Trust model, as it seeks to ensure that only trusted and secure devices gain access to critical applications, reducing the attack surface and enhancing overall security posture. Duo’s Trusted Endpoints ensures that only company-approved devices can access applications, while the integration with Cisco Secure Endpoint can block the compromised device until it has been remediated.
How Duo Trusted Endpoints and Cisco Endpoint work together
Any Duo-protected application that uses the Duo Prompt can prohibit access by checking the endpoint’s status in the Cisco Secure Endpoint Dashboard during the authentication.
Here's how it works:
1. Lee (the end user) logs into a Duo-protected application using primary authentication
2. Duo checks to see if Lee and the application are subject to a Trusted Endpoints policy
3. If they are, Duo checks to see if the endpoint is trusted (via AD DS, Jamf or other supported integrations)
4. If the endpoint is trusted, Duo checks the hostname of the device against Cisco Secure Endpoint via API call
5. Cisco Secure Endpoint will report to Duo if the endpoint is in a compromised state or not
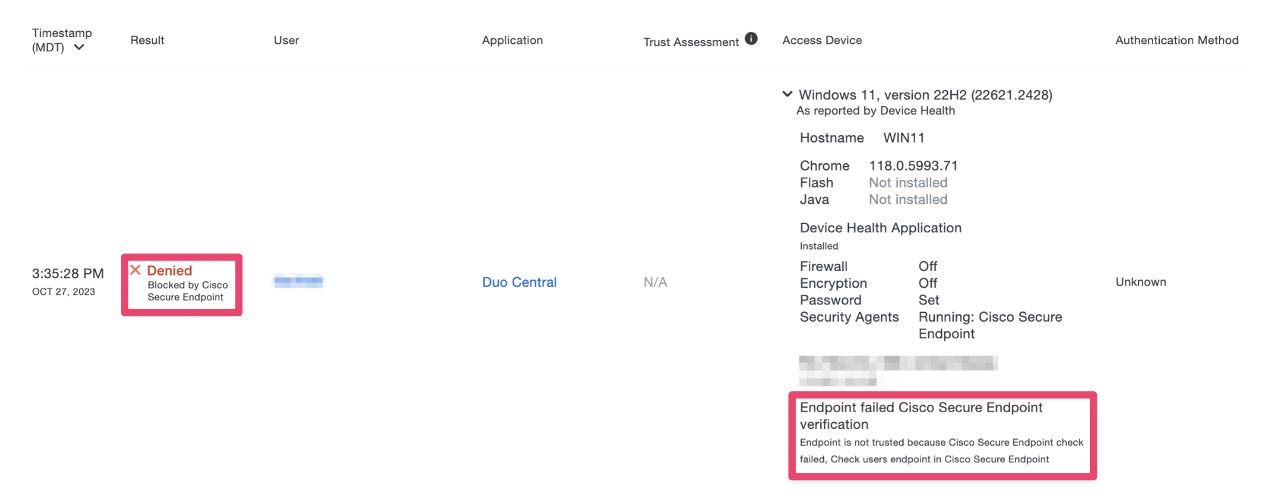
6. If the endpoint is marked as compromised, Duo will prevent Lee from authenticating via secondary authentication. Steps 2 through 6 all occur within just a few seconds!
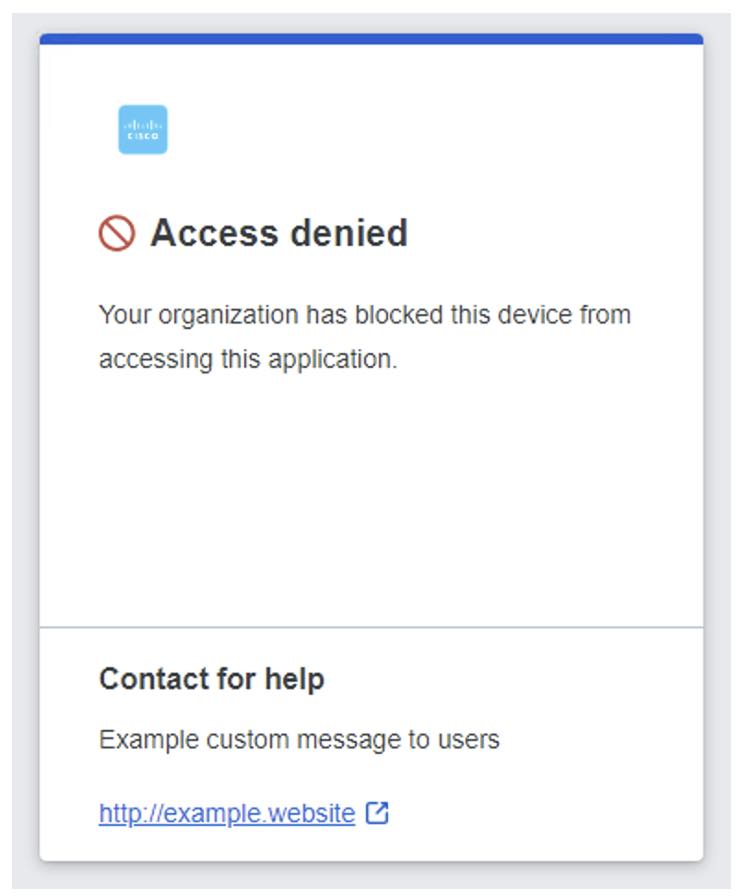
7. Lee contact the Help Desk and the Security Team performs their investigation of the endpoint
8. Once the Security Team completes the remediation, they mark it as “Resolved” in the triage inbox inside of the Cisco Secure Endpoint Dashboard
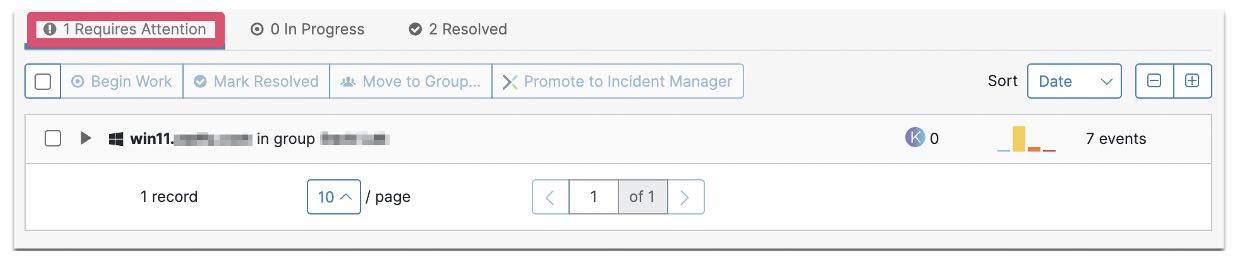
9. Lee logs in again and Duo runs the same process (steps 2-6) to determine if the access device is trusted and uncompromised
10. If all looks good, Lee is permitted to complete secondary authentication in order to access the application
Check out Duo’s interactive demo of this process.
For detailed documentation, please reference Duo Trusted Endpoints - Cisco Secure Endpoint.
Conclusion
Endpoint security is an essential component of a comprehensive application security strategy. By understanding the risks associated with compromised endpoints and implementing Duo Trusted Endpoints along with Cisco Secure Endpoint, organizations can protect sensitive data, mitigate insider threats, prevent device-based attacks, and enforce a Zero Trust model. Duo Care customers can count on their Customer Success Manager (CSM) and Customer Solutions Engineer (CSE) to help them prioritize endpoint security, which safeguards the entire application ecosystem and ensures a secure digital environment for all users.
Be safe out there!

