Duo Care is Here to Help with Trusted Endpoints
At any given point in time, the Duo Care teams are having conversations with customers that span the spectrum of security topics. We love being able to work with organizations who are just getting started with Duo, as well as work with organizations who are looking to build more comprehensive protection on top of an initial MFA deployment.
What have we been most excited to talk to our customers about recently? Access Management and Trusted Endpoints.
Access Management Is Essential to Cybersecurity Excellence
In Case You Missed It (ICYMI) over the last handful of years, cybercriminals have stepped up their game, particularly when it comes to attacking weaker MFA implementations ... but as you read in previous blogs, Duo has been upping its game too.
Duo has released features like Risk-Based Authentication and Verified Duo Push, added features like OIDC to Single-Sign-On, and expanded support for Passwordless – all of which can help organizations have more comprehensive protections in place.
Another key step in directly combatting the recent MFA focused attacks is evaluating whether the device can be trusted. That is why Duo Care has been so excited about the expansion of Duo’s Trusted Endpoints feature to all editions – Essentials, Advantage, and Premier.
By implementing Trusted Endpoints, organizations can differentiate between managed and unmanaged devices and set policies accordingly – giving you the option to block access from unknown devices and only allow trusted devices to gain access to sensitive applications and resources. Not only does this give organizations better control to ensure access devices meet your security standards, but it also provides further protection from social engineering attacks.
Fast Track to Success with Duo Care
The Duo Care Premium Support Program was created because we really do care. The dedicated Customer Success Managers and Customer Solutions Engineers who make up the Duo Care teams strive to be true trusted advisors to organizations who are using Duo. It is in that role that we have been so excited to talk to everyone about Trusted Endpoints.
It is true that Duo’s product has long been loved for how fast deployment is and how easy solutions are to use – and the Trusted Endpoints feature is no different. Still, organizations working with Duo Care will have a dedicated partner every step along the way.
We have end user communication templates that will make explaining this new feature to your organization a breeze and will share plenty of best practices, so you can be confident in the plan. Check out this sample timeline of a customer rolling out Trusted Endpoints:
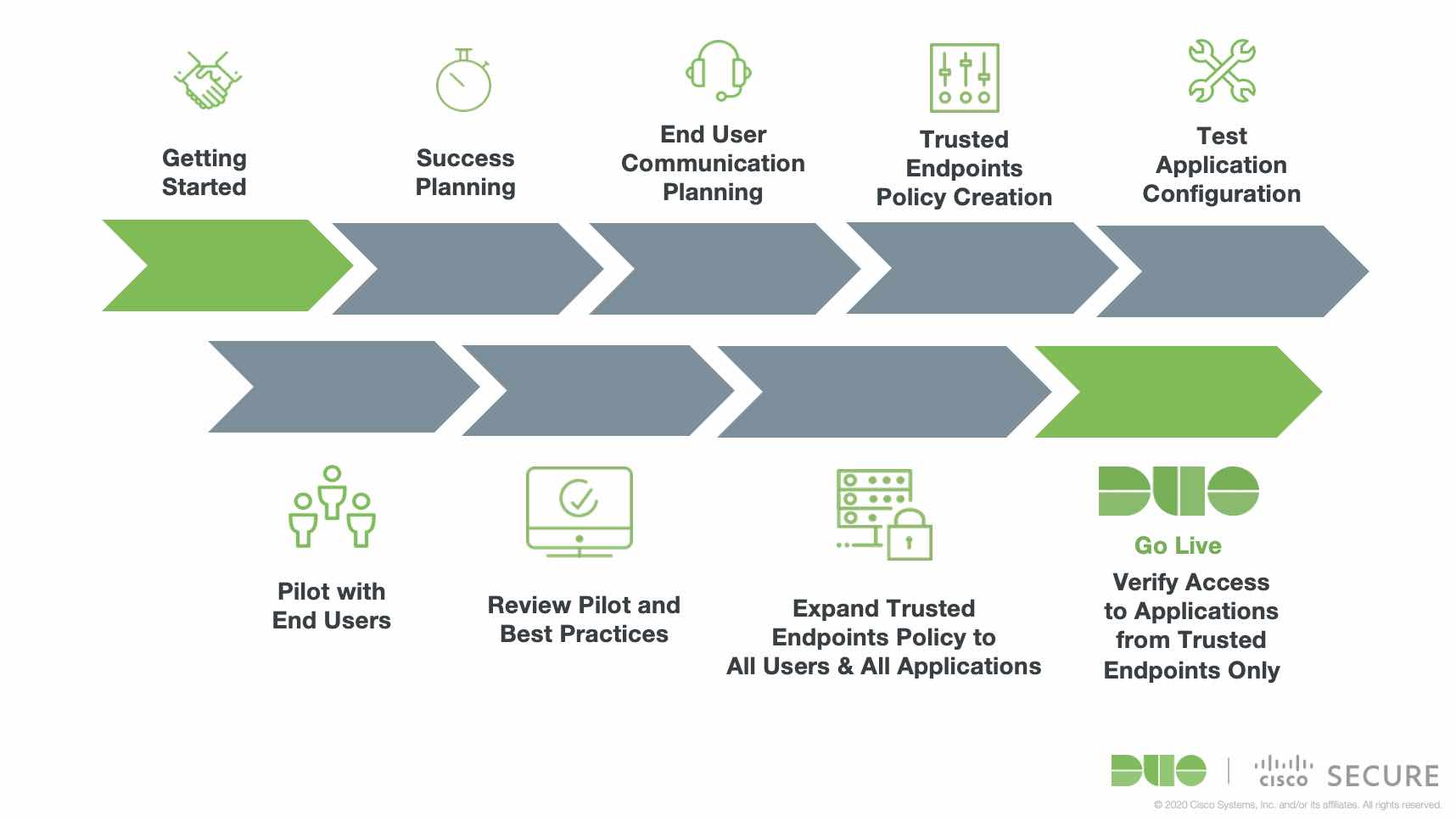
Duo Care will meet with your team to strategize around any nuances of a more complex environment and make sure to answer any questions that you might have about how Trusted Endpoints will fit into your overall security plan.
For Duo customers on the Advantage and Premier editions, this might include discussing more about Device Health Checks (Is this device’s operating system up to date?) and Endpoint Protection Checks (Does this trusted and healthy device have an endpoint protection agent like Cisco Secure Endpoint agent installed?) in addition to the Trusted Endpoints Check (Is this user’s device managed/registered?).
Ready to take the next step?
If you are just as excited as we are about the Trusted Endpoints feature, take action today!
Duo Care Customers
Send an email to your Customer Success Manager – alongside your dedicated Customer Solutions Engineer, they will be ready to schedule a call to help you get started!
All Other Paid Subscribers
If you are interested in adding Duo Care Premium Support to your current contract, please send an email to your Duo Account Executive or Cisco Account Manager.

